What is this?
EnigmaSync is a comprehensive encryption and verification system that ensures secure data transmission between applications and servers. It utilizes AES encryption, secure token generation, and real-time verification checks to maintain data integrity and confidentiality. Whether you're developing a new application or enhancing an existing one, EnigmaSync offers the tools needed to protect your data.
Summary
In today's digital age, ensuring the security of data transmission is more crucial than ever. Enter EnigmaSync, an advanced encryption and verification system designed to safeguard your data. This project leverages robust encryption algorithms, secure communication protocols, and real-time verification to provide unparalleled protection for your sensitive information.
-
Year
2024
-
Client
PythonP Software
-
Services
Secure Login Solution
-
Project
EnigmaSync
Description
Initialization and Configuration
The process begins with setting up the environment and configuring EnigmaSync parameters such as the secret key, version, hardware ID (HWID), and base URLs for login and verification checks. EnigmaSync does not use a local login page; all login processes go through the secure website directly, enhancing security by centralizing authentication.
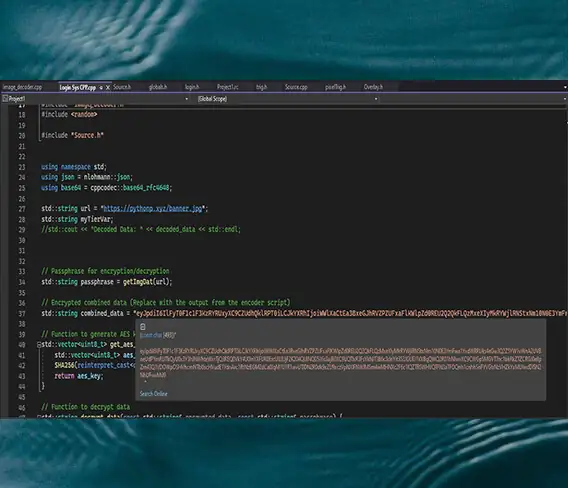
AES Encryption
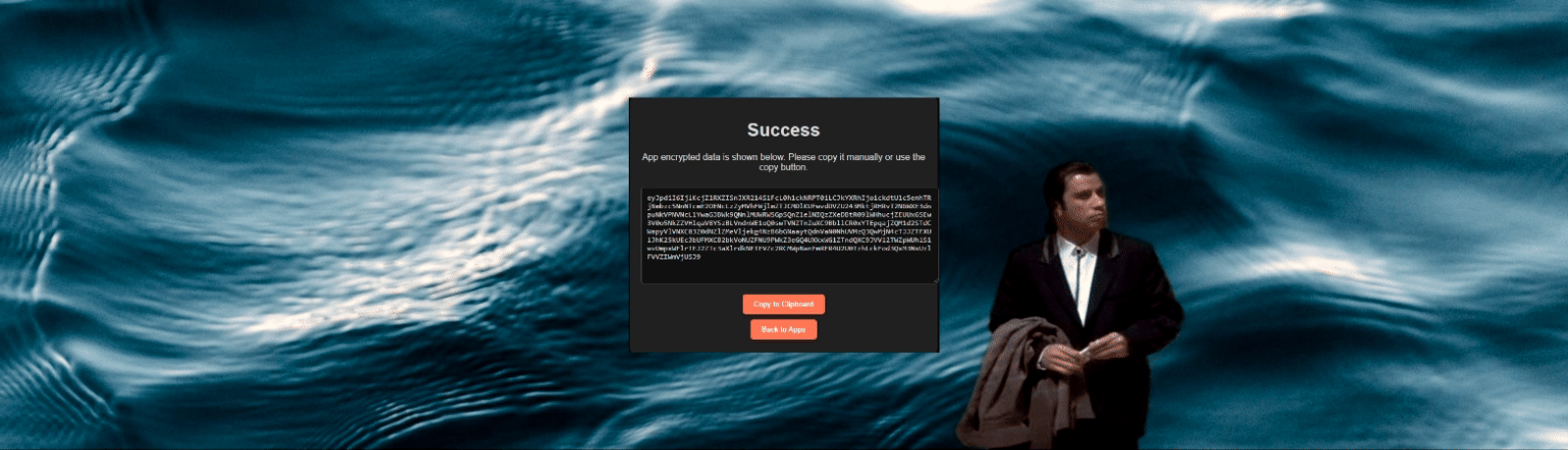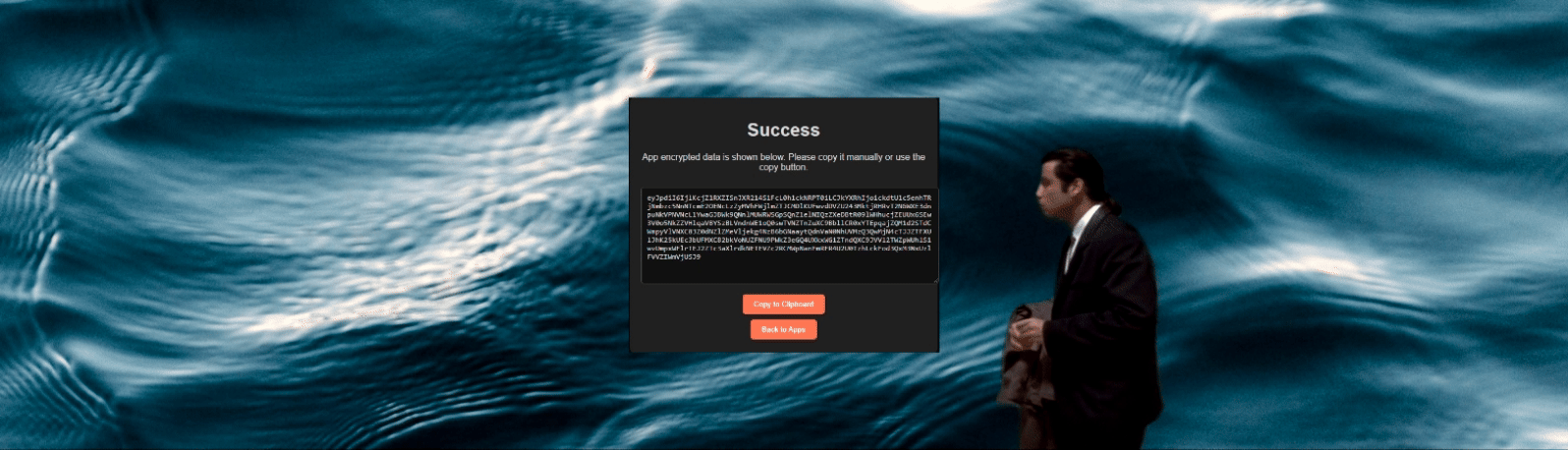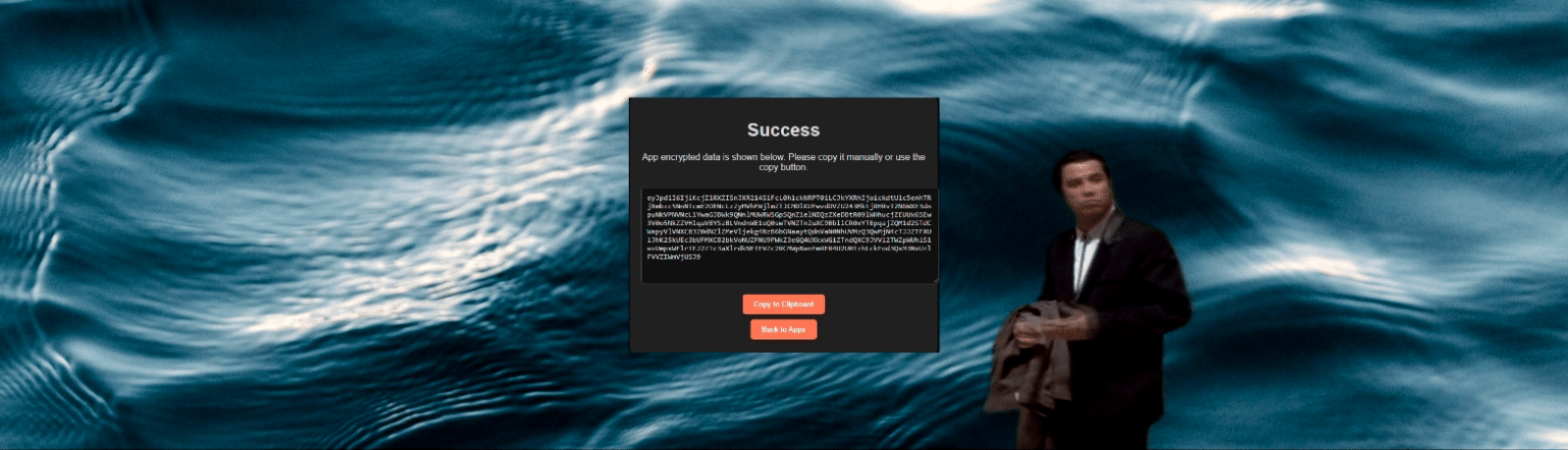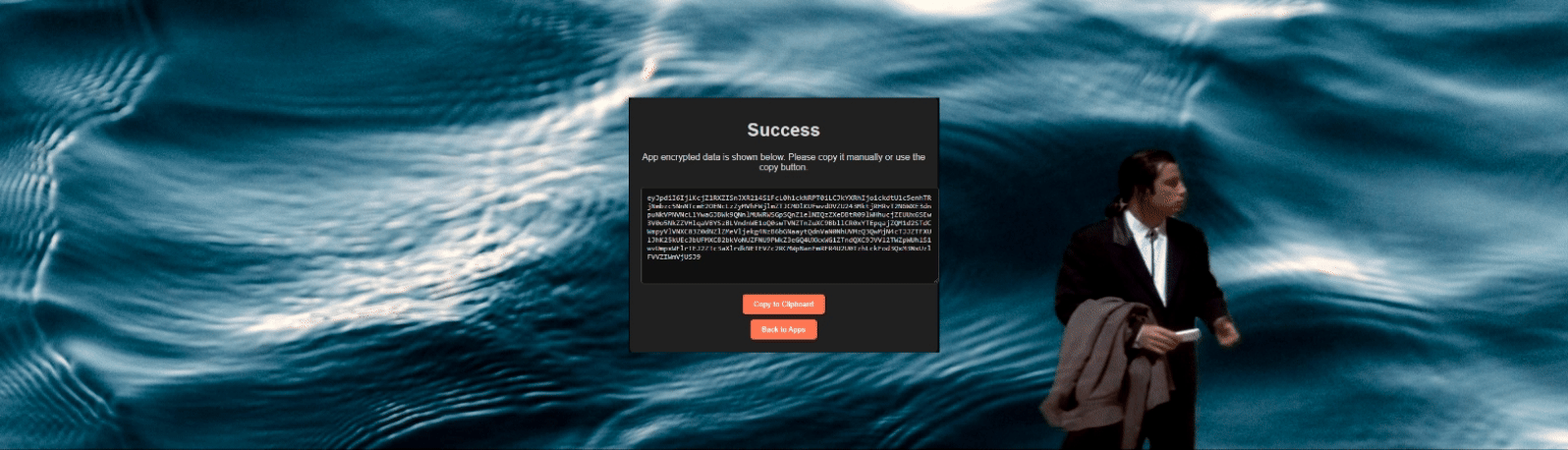
EnigmaSync employs Advanced Encryption Standard (AES) to encrypt data. A secret key, derived from a secure passphrase using SHA-256 hashing, is used to create a cipher. Data is padded and encrypted using this cipher, ensuring robust protection against unauthorized access.
Token Generation and Session Management
A secure token is generated for each session, ensuring that every interaction is uniquely identified and authenticated. This token is included in all communication to verify the legitimacy of the session.
Real-Time Verification
EnigmaSync performs real-time verification checks using a secure 'ping pong' communication protocol. This ensures continuous monitoring and validation of data integrity, synchronizing time across different time zones to prevent replay attacks.
Data Encryption and Decryption
Data sent to the server is combined and encrypted into a single string using the AES encryption method. On the server side, the data is decrypted and validated, ensuring that only authorized and intact data is processed.
Thread Monitoring and Redundant Security
A dedicated background thread monitors the integrity of the communication. If anomalies or tampering attempts are detected, secondary security measures are activated to maintain the system's robustness.
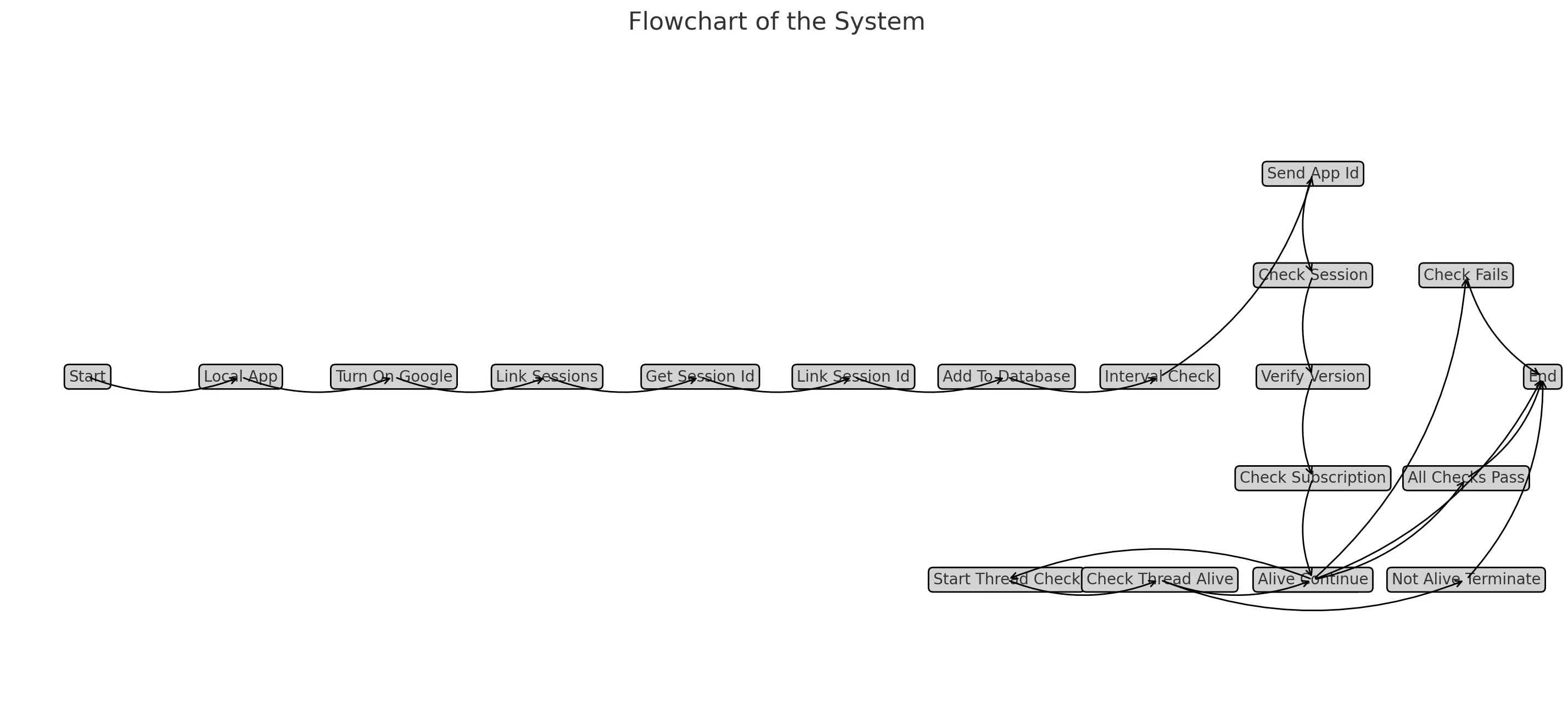
Step-by-Step Guide on How EnigmaSync Works
Setting Up EnigmaSync
EnigmaSync begins by initializing various parameters such as the secret key, version, hardware ID, and base URLs. These parameters are crucial for ensuring secure communication between the client and server.
Generating a Secure Token
Once the initial setup is complete, EnigmaSync generates a secure session token. This token is a unique identifier for each session, ensuring that every interaction is authenticated.
Encrypting Data
EnigmaSync uses AES encryption to protect data. The data is first padded to match the block size of the AES algorithm, then encrypted using a cipher created from the secret key.
Combining and Encrypting Parameters
All session parameters are combined into a single string and encrypted. This ensures that the data transmitted to the server is secure and cannot be intercepted or tampered with.
Including Time in Data Transmission
To prevent replay attacks, EnigmaSync includes a timestamp in the data sent to the server. This ensures that even if the data is intercepted, it cannot be reused at a later time.
Linking Session IDs
The encrypted session parameters are sent to the server to establish a secure session. This step ensures that both the client and server are synchronized and authenticated.
Performing Real-Time Verification
Throughout the session, EnigmaSync performs continuous real-time verification checks. This is done using a secure 'ping pong' protocol that synchronizes data and time between the client and server.
Monitoring Communication Integrity
A background thread continuously monitors the communication for any anomalies or tampering attempts. If any issues are detected, secondary security measures are activated to ensure the integrity of the system.
Additional Security Thread
Another thread checks if the live verification function is actively running, providing an additional layer of security to prevent reverse engineering attempts.
Decrypting and Validating Data
On the server side, the encrypted data is decrypted and validated. This ensures that only authorized data is processed and any unauthorized attempts are detected and mitigated.


 EnigmaSync
EnigmaSync